Salesforce Xss Protection
Salesforce xss protection. Please support me on Patreon. I saw that it can impact on applications that uses Visualforce. For example the following code is normally vulnerable to an XSS attack because it takes user-supplied input and outputs it directly back to the user but the tag is XSS-safe.
Enable Cross-Site Scripting XSS Protection. Use one of two basic techniques to do this. For the developer using standard classes and output methods the threats of XSS flaws have been largely mitigated.
The X-XSS-Protection header is designed to enable the cross-site scripting XSS filter built into modern web browsers. All standard Visualforce components which start with have anti-XSS filters in place to screen out harmful characters. This header prevents some Reflected Cross-Site Scripting attacks.
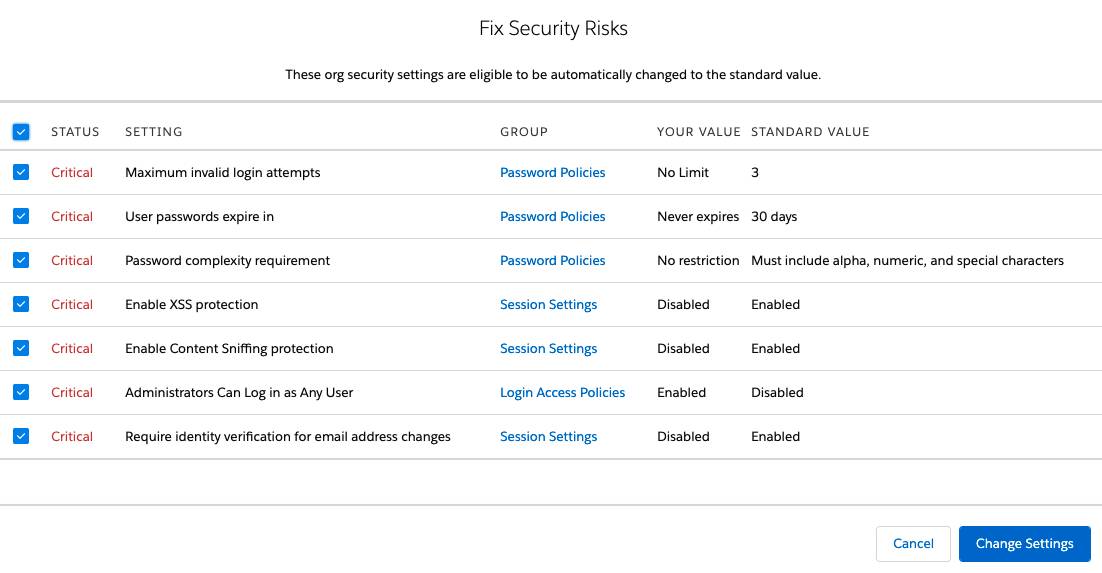
The HTTP header can be turned on or off by each organization under Setup Security Controls Session Settings Enable XSS Protection. In order to add security to our Spring Boot application we need to add the security starter dependency. From Setup in the Quick Find box search for Session Settings.
Now that youve seen the dangers that XSS poses to your users well arm you with defense mechanisms that you can use in your application to protect against these attacks. Im reviewing a clients Health Check and Id like to know what are the impacts after enabling XSS and Content Sniffing protection on the organization. Modifies the email or event in Exchange to include the Salesforce record ID in the extended properties of the Exchange object.
Setting X-XSS-Protection response headers in Apex has no effectHelpful. It is supported by Internet Explorer 8 Chrome and Safari. However Salesforce Developers rarely go into the specifics and for good reason however their code-scanner plugin that runs PMD still detects XSS vulnerabilities and it is difficult to know what kind of XSS scripting that we are dealing with stored or reflective.
If there is no content scripts cannot be used to inject attacks. Impact on enabling XSS and Content Sniffing protection.
For example the following code is normally vulnerable to an XSS attack because it takes user-supplied input and outputs it directly back to the user but the tag is XSS-safe.
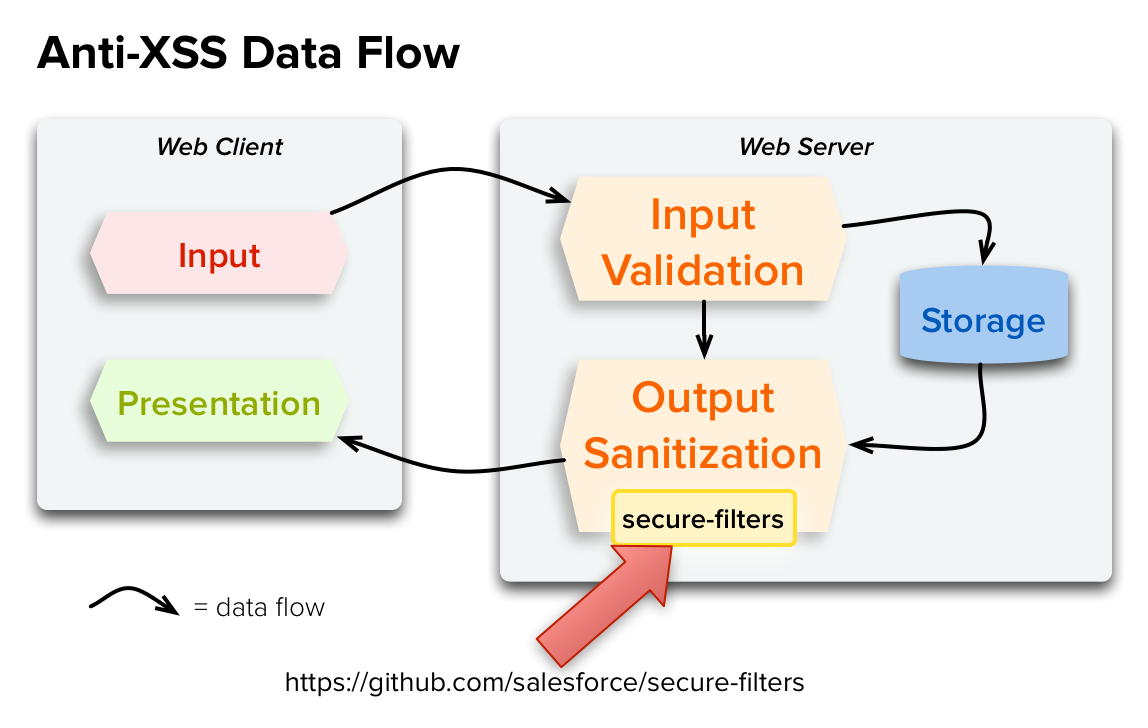
Within the Lightning Platform there are several anti-XSS defenses in place. Input filtering and output encoding. If a reflected cross-site scripting attack is detected the browser shows a blank page with no content. It works with the. Now that youve seen the dangers that XSS poses to your users well arm you with defense mechanisms that you can use in your application to protect against these attacks. Enable the XSS protection setting to protect against reflected cross-site scripting attacks. Select Enable XSS protection to protect against cross-site scripting attacks. I saw that it can impact on applications that uses Visualforce. For example the following code is normally vulnerable to an XSS attack because it takes user-supplied input and outputs it directly back to the user but the tag is XSS-safe.
Im reviewing a clients Health Check and Id like to know what are the impacts after enabling XSS and Content Sniffing protection on the organization. It is supported by Internet Explorer 8 Chrome and Safari. The HTTP header can be turned on or off by each organization under Setup Security Controls Session Settings Enable XSS Protection. XSS is caused by weak separation between code context the actual commands and variables used in a program and user data the input from a user. It works with the. Select Enable Content Sniffing protection to prevent the browser from inferring the MIME type from the document content. After these conditions are met images and other content will load successfully for users accessing Salesforce using Safari 131.
































Post a Comment for "Salesforce Xss Protection"